Reverse-BoX
记一次做题遇到的问题,题目给了目的,即令程序输出
1 | 95eeaf95ef94234999582f722f492f72b19a7aaf72e6e776b57aee722fe77ab5ad9aaeb156729676ae7a236d99b1df4a |
对程序进行分析,发现,我们输入的命令行参数字符的ASCII值作为盒子的索引
首先主函数将一个变量的地址交给盒子,进去,有个取随机值的运算,且取得随机值仅为1字节,那么我们只有256种可能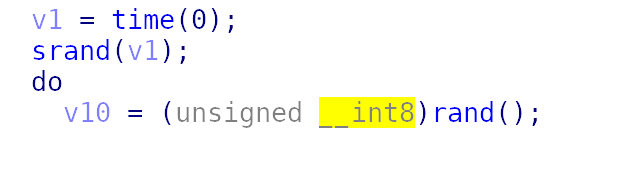
所以我们采用爆破,令随机值在[0,256],逐个检测,直到输出的字符串与上述前面部分相等
思路
1.利用Gdb脚本爆破,输出时,若出现0x95即可停止
2.Dump出盒子的256个字节的内容
3.利用结果在盒子里面查找,确定结果的每个字节在盒子里面的索引
利用
贴出Gdb脚本,取的别人的脚本,在此感谢原脚本作者
1 | set $i=0 |
2 | set $total=256 |
3 | while($i<$total) |
4 | b *0x80485b4 #取随机值处 |
5 | b *0x8048704 #打印字节处 |
6 | run T |
7 | set $i=$i+1 |
8 | set *(char*)($ebp-0xC)=$i |
9 | continue |
10 | if ($eax==0x95) |
11 | print $i, $i |
12 | x/256xb $esp+0x1C #main函数里,盒子的栈地址 |
13 | set $i=256 |
14 | end |
15 | stop |
16 | end |
保存为文本,gdb调试时,用source加载上述含有爆破脚本的文本即可开始
确定盒子的内容,得到如下的盒子:
1 | List = [ |
2 | 0xd6,0xc9,0xc2,0xce,0x47,0xde,0xda,0x70, |
3 | 0x85,0xb4,0xd2,0x9e,0x4b,0x62,0x1e,0xc3, |
4 | 0x7f,0x37,0x7c,0xc8,0x4f,0xec,0xf2,0x45, |
5 | 0x18,0x61,0x17,0x1a,0x29,0x11,0xc7,0x75, |
6 | 0x02,0x48,0x26,0x93,0x83,0x8a,0x42,0x79, |
7 | 0x81,0x10,0x50,0x44,0xc4,0x6d,0x84,0xa0, |
8 | 0xb1,0x72,0x96,0x76,0xad,0x23,0xb0,0x2f, |
9 | 0xb2,0xa7,0x35,0x57,0x5e,0x92,0x07,0xc0, |
10 | 0xbc,0x36,0x99,0xaf,0xae,0xdb,0xef,0x15, |
11 | 0xe7,0x8e,0x63,0x06,0x9c,0x56,0x9a,0x31, |
12 | 0xe6,0x64,0xb5,0x58,0x95,0x49,0x04,0xee, |
13 | 0xdf,0x7e,0x0b,0x8c,0xff,0xf9,0xed,0x7a, |
14 | 0x65,0x5a,0x1f,0x4e,0xf6,0xf8,0x86,0x30, |
15 | 0xf0,0x4c,0xb7,0xca,0xe5,0x89,0x2a,0x1d, |
16 | 0xe4,0x16,0xf5,0x3a,0x27,0x28,0x8d,0x40, |
17 | 0x09,0x03,0x6f,0x94,0xa5,0x4a,0x46,0x67, |
18 | 0x78,0xb9,0xa6,0x59,0xea,0x22,0xf1,0xa2, |
19 | 0x71,0x12,0xcb,0x88,0xd1,0xe8,0xac,0xc6, |
20 | 0xd5,0x34,0xfa,0x69,0x97,0x9f,0x25,0x3d, |
21 | 0xf3,0x5b,0x0d,0xa1,0x6b,0xeb,0xbe,0x6e, |
22 | 0x55,0x87,0x8f,0xbf,0xfc,0xb3,0x91,0xe9, |
23 | 0x77,0x66,0x19,0xd7,0x24,0x20,0x51,0xcc, |
24 | 0x52,0x7d,0x82,0xd8,0x38,0x60,0xfb,0x1c, |
25 | 0xd9,0xe3,0x41,0x5f,0xd0,0xcf,0x1b,0xbd, |
26 | 0x0f,0xcd,0x90,0x9b,0xa9,0x13,0x01,0x73, |
27 | 0x5d,0x68,0xc1,0xaa,0xfe,0x08,0x3e,0x3f, |
28 | 0xc5,0x8b,0x00,0xd3,0xfd,0xb6,0x43,0xbb, |
29 | 0xd4,0x80,0xe2,0x0c,0x33,0x74,0xa8,0x2b, |
30 | 0x54,0x4d,0x2d,0xa4,0xdc,0x6c,0x3b,0x21, |
31 | 0x2e,0xab,0x32,0x5c,0x7b,0xe0,0x9d,0x6a, |
32 | 0x39,0x14,0x3c,0xb8,0x0a,0x53,0xf7,0xdd, |
33 | 0xf4,0x2c,0x98,0xba,0x05,0xe1,0x0e,0xa3,] |
最后写Py脚本进行解密:
1 | List = [ |
2 | 0xd6,0xc9,0xc2,0xce,0x47,0xde,0xda,0x70, |
3 | 0x85,0xb4,0xd2,0x9e,0x4b,0x62,0x1e,0xc3, |
4 | 0x7f,0x37,0x7c,0xc8,0x4f,0xec,0xf2,0x45, |
5 | 0x18,0x61,0x17,0x1a,0x29,0x11,0xc7,0x75, |
6 | 0x02,0x48,0x26,0x93,0x83,0x8a,0x42,0x79, |
7 | 0x81,0x10,0x50,0x44,0xc4,0x6d,0x84,0xa0, |
8 | 0xb1,0x72,0x96,0x76,0xad,0x23,0xb0,0x2f, |
9 | 0xb2,0xa7,0x35,0x57,0x5e,0x92,0x07,0xc0, |
10 | 0xbc,0x36,0x99,0xaf,0xae,0xdb,0xef,0x15, |
11 | 0xe7,0x8e,0x63,0x06,0x9c,0x56,0x9a,0x31, |
12 | 0xe6,0x64,0xb5,0x58,0x95,0x49,0x04,0xee, |
13 | 0xdf,0x7e,0x0b,0x8c,0xff,0xf9,0xed,0x7a, |
14 | 0x65,0x5a,0x1f,0x4e,0xf6,0xf8,0x86,0x30, |
15 | 0xf0,0x4c,0xb7,0xca,0xe5,0x89,0x2a,0x1d, |
16 | 0xe4,0x16,0xf5,0x3a,0x27,0x28,0x8d,0x40, |
17 | 0x09,0x03,0x6f,0x94,0xa5,0x4a,0x46,0x67, |
18 | 0x78,0xb9,0xa6,0x59,0xea,0x22,0xf1,0xa2, |
19 | 0x71,0x12,0xcb,0x88,0xd1,0xe8,0xac,0xc6, |
20 | 0xd5,0x34,0xfa,0x69,0x97,0x9f,0x25,0x3d, |
21 | 0xf3,0x5b,0x0d,0xa1,0x6b,0xeb,0xbe,0x6e, |
22 | 0x55,0x87,0x8f,0xbf,0xfc,0xb3,0x91,0xe9, |
23 | 0x77,0x66,0x19,0xd7,0x24,0x20,0x51,0xcc, |
24 | 0x52,0x7d,0x82,0xd8,0x38,0x60,0xfb,0x1c, |
25 | 0xd9,0xe3,0x41,0x5f,0xd0,0xcf,0x1b,0xbd, |
26 | 0x0f,0xcd,0x90,0x9b,0xa9,0x13,0x01,0x73, |
27 | 0x5d,0x68,0xc1,0xaa,0xfe,0x08,0x3e,0x3f, |
28 | 0xc5,0x8b,0x00,0xd3,0xfd,0xb6,0x43,0xbb, |
29 | 0xd4,0x80,0xe2,0x0c,0x33,0x74,0xa8,0x2b, |
30 | 0x54,0x4d,0x2d,0xa4,0xdc,0x6c,0x3b,0x21, |
31 | 0x2e,0xab,0x32,0x5c,0x7b,0xe0,0x9d,0x6a, |
32 | 0x39,0x14,0x3c,0xb8,0x0a,0x53,0xf7,0xdd, |
33 | 0xf4,0x2c,0x98,0xba,0x05,0xe1,0x0e,0xa3,] |
34 | result = '' |
35 | s = '95eeaf95ef94234999582f722f492f72b19a7aaf72e6e776b57aee722fe77ab5ad9aaeb156729676ae7a236d99b1df4a' |
36 | for i in range(0, len(s), 2): |
37 | s1 = int(s[i:i+2], 16) |
38 | #print s1 |
39 | result += chr(List.index(s1)) |
40 | print (result) |
生产的Flag为:
1 | TWCTF{5UBS717U710N_C1PH3R_W17H_R4ND0M123D_5-B0X} |